CVE-2021-3156 - SUDO grants root access to attackers! Here is the fix - package update details for various Operating systems
Description
Sudo before 1.9.5p2 has a Heap-based Buffer Overflow, allowing privilege escalation to root via "sudoedit -s" and a command-line argument that ends with a single backslash character.
What Does this mean?
A heap overflow vulnerability affecting all major Unix-like operating systems. This flaw is exploitable by any local user (normal users and system users, sudoers and non-sudoers), without authentication (i.e., the attacker does not need to know the user's password). Successful exploitation of this flaw could lead to privilege escalation.
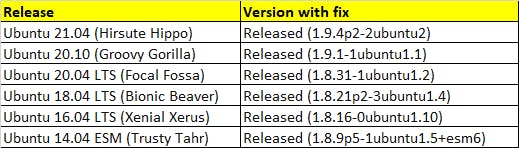
Update sudo on Ubuntu
$ apt-get update
$ apt-get --only-upgrade install sudo
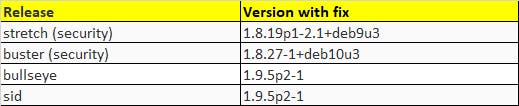
Update sudo on Debian
$ apt-get update
$ apt-get --only-upgrade install sudo
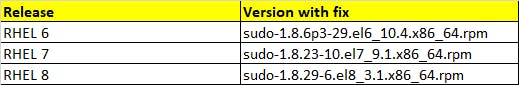
Update sudo on RHEL
$ yum update sudo
References:
- NIST - cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-..
- security-tracker.debian.org/tracker/DLA-253..
- security-tracker.debian.org/tracker/DSA-483..
- ubuntu.com/security/notices/USN-4705-1
- access.redhat.com/errata/RHSA-2021:0221
- access.redhat.com/errata/RHSA-2021:0227
- access.redhat.com/errata/RHSA-2021:0218
Thanks!
Stay tuned for more!